Technology
In a Test, Apple AirTag Trackers Made It Terrifyingly Simple to ‘Follow’ Me.

Table of Contents

Apple AirTags, which cost $30 and help you find items, function wonderfully. Surprisingly good.
If you attach a button-sized AirTag on your keys, it will help you find them if you drop them in the park. However, if someone sneaks an AirTag into your backpack or car without your knowledge, it might be used to monitor you everywhere you go invisibly. Apple AirTags is a new way of stalking that is both affordable and effective, in addition to helping you recover missing objects.
I know because I put AirTags to the test by having a UpdatedTime Post colleague pose as a stalker. Apple’s efforts to prevent the exploitation of its trackers just aren’t enough.
Apple put technologies into AirTags to notify prospective victims of “unwanted tracking,” including audio alarms and warnings about suspicious AirTags that come up on iPhones. My colleague Jack Caristo linked an AirTag with his iPhone, slid his tag into my bag (with my consent), and then monitored me for a week from across San Francisco Bay.
I received many warnings, both on my iPhone and through the disguised AirTag. However, it wasn’t difficult to uncover ways for an abusive spouse to get beyond Apple’s security measures. To give you an example: After three days, the sound alarm finally went off — and it was just 15 seconds of gentle chirping. Another example: While an iPhone warned me that an unknown AirTag was following me, comparable alerts aren’t accessible for the approximately half of Americans who own Android phones.
In an interview, Kaiann Drance, Apple vice president of iPhone marketing, remarked, “These are an industry-first, robust set of proactive deterrents.” “It’s a clever and customizable system, and we can keep refining the logic and timing to increase the set of deterrents,” says the researcher.
Apple has taken more steps to discourage stalking than smaller tracking-device competitors like Tile, which has done nothing thus far. AirTags, on the other hand, demonstrates how even Apple, a firm known for prioritizing security and privacy, may fail to comprehend all of the hazards inherent in developing technology that connects common objects to the internet.
“The intimate partner threat model is unique,” Corbin Streett, a technology safety specialist with the National Network to End Domestic Violence, told me. In general, companies are worried about their external environment. dangers, not with the individual who knows your favorite color and password and sleeps next to you at night.”
Apple AirTags will be a valuable convenience for most individuals, as they provide accurate tracking and a changeable battery. So what’s the point of focusing on these issues? Because personal technology isn’t just about you anymore. As a consumer advocate, it’s my responsibility to think about who technology benefits and who it damages. This is true of Apple AirTags, as well as Ring security cameras that unjustly police neighbors and social media algorithms that disseminate disinformation.
Experts warn that digital stalking is quite widespread and that it is directly connected to physical assault, even murder.
“I don’t expect products to be perfect the moment they hit the market,” said Eva Galperin, director of cybersecurity at the Electronic Frontier Foundation and a vocal opponent of the stalker was. “I don’t believe they would have taken the decisions they did if they had consulted even one specialist on intimate partner abuse,” she continued.
Drance refused to answer if Apple engaged domestic abuse experts before developing AirTags. “We don’t have any further information regarding the procedure to share.” “Of course, we’re interested in hearing from such groups,” she added.

I’m delighted Apple claims AirTags was created for updates, but some of the issues we found can’t be remedied with software — or with Apple inventing privacy remedies that only work for Apple consumers.
A Massive Network
We set up a test with Galperin’s help, in which my colleague acted like a stalker and I experienced what it would be like to be a target. While the experiment gave us a better understanding of how AirTags function, our little view into the realm of the stalker was paled in comparison to the dread of being stalked.
My colleague was able to pinpoint my whereabouts with astonishing accuracy after inserting an Apple AirTag in my backpack. When he linked the Apple AirTag to his iPhone, the tag’s location appeared in the Find My app, which comes pre-installed on all iPhones. (It began as a tool to locate misplaced Apple devices and has now extended to include other items.)
The Apple AirTag updated my location once every several minutes while I was riding my bike around San Francisco, with a range of around half a block. When I was at home and more sedentary My precise address was supplied on a colleague’s app.
How is it possible for such a little, watch battery-powered gadget to do such feats? AirTags, unlike phones and GPS devices, do not have cellular Internet access. Rather, they employ Bluetooth wireless signals — the same ones that power headphones — to alert other nearby Internet-connected gadgets to their existence. (AirTags also include ultra-wideband wireless technology, which makes them even more exact but requires newer iPhones.) Only the AirTag’s owner receives these location notifications; no one else is aware of their whereabouts.
The fact that AirTags can link with the hundreds of millions of Apple goods on the market to transmit their whereabouts with their owners makes them extremely efficient at tracking. Consider the following scenario: AirTags function everywhere an iPhone is within range.
Apple added one feature that might aid in the prosecution of persons who use their products for stalking. A fixed serial number is physically printed on each AirTag and is readable by Bluetooth. Apple might expose the identity of the iPhone the AirTag is registered if a court order is obtained.
However, the victim would have to first uncover the hidden AirTag, which is tougher said than done.
What Is That Noise?

The Apple AirTag he implanted on me began chirping its presence three days after I was separated from him. (You can hear it in the video that goes with this article.)
From three feet away, the sound measured at most 60 dB, which isn’t much louder than the birds chirping outside my window. It barely lasted approximately 15 seconds before the AirTag was silent for several hours before chirping again for another 15 seconds.
Isn’t this intended to protect people? Apple’s Drance remarked, “We do believe it’s a really clean, sharp sound.”
Worse, I discovered that pressing down on the AirTag’s white plastic cover, which has the speaker built in it, is a simple way to mute the speaker. A victim may not detect a chirping AirTag for days, if at all if he or she is encased in tight automobile seats or tape.
However, there’s a deeper issue: waiting three days to notify a victim allows for a lot of surveillance. When Apple picked that timeframe, Drance said the firm considered how alarms can annoy consumers who are only borrowing a family member’s rucksack or have mistakenly left an item behind. “We wanted to strike a balance between how these warnings go off in the environment and the unwanted tracking,” she explained.
Streett was concerned that an abuser may manipulate the alarm’s time. When an AirTag leaves the range of the iPhone it’s associated with, it sets off a three-day countdown clock on its alarm. Because many victims live with their abusers, the alert countdown might be restarted each night when the AirTag’s owner returns within range.
In many cases of abuse, the warning may never sound at all.
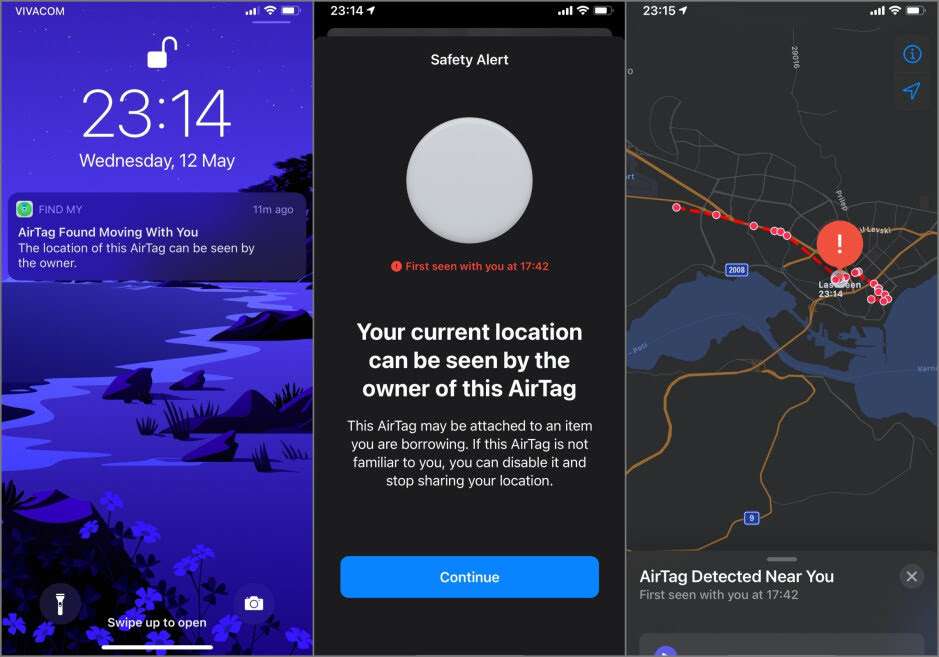
Notice that appears in the middle of the screen
![]()
The second key anti-stalking feature from Apple was more difficult to overlook: a notice on my iPhone that stated, “AirTag Found Moving With You.” It appeared when I got home after a meeting with a colleague.
How did my iPhone figure that out? If you have an iPhone 6S or newer with the current iOS software, the phone’s Bluetooth connection will seek nearby AirTags on a frequent basis. If you’re traveling with an AirTag that isn’t with its owner, the iPhone will detect it.
If the wording is a little convoluted, the iPhone helps these alerts stand out. When you tap it, you’ll be sent to the Find My app, where the first page says, “The owner of this AirTag may view your current position.” There was also a map of the areas I went to with the hidden Apple AirTag inside the Find My app, which was viewed by the possible victim. The software shows you how to disable the AirTag or temporarily quiet the warning by removing the battery.
Apple, on the other hand, doesn’t offer as much assistance as it might to those looking for an AirTag buried in their possessions. The offending AirTag can be made to create a sound using a button in the Find My app, however, this didn’t always work for me. (Perhaps there was interference or I wasn’t close enough to the AirTag?) However, none of the additional Find My app features allowing AirTag owners to locate their belongings, such as distance measurements between the iPhone and the AirTag, are available to unwanted track victims. Those tools are also required by potential victims.
The Find My app does not always give all of the information that stalker victims require. “I hope it would activate as soon as a tag that isn’t yours starts moving with you,” Streett remarked. The software also lacks a feature that allows users to quickly scan their surroundings for any AirTags to ensure their safety.
Galperin is suspicious that Apple considered all possible possibilities, such as an abuser swapping his AirTag with one belonging to his girlfriend. (If the victim returned to the house and the device rapidly linked to the abuser’s device, the alarm may not appear.) The warnings may potentially be more useful if they were adjusted to identify an AirTag in your car — one that moves with you regularly but then remains put where you parked, she added.
CLICK HERE: FOR MORE READING ABOUT UPDATED TIME
Also troubling: You can turn off all of these “item safety warnings” via the Find My app, and you don’t have to input your PIN or password to do so. People who are subjected to abuse do not always have complete control over their phones.
Then there’s the main flaw in the alert system: Android users aren’t able to use it. “I’m quite concerned about security issues that must be resolved by purchasing an iPhone,” Galperin stated.
Some of Apple’s smart pop-up alert ideas might help not only iPhone users but also those who are followed by other devices like Tile. “Wouldn’t it be amazing if these companies banded together in such a way that all phones have built-in scanning for Bluetooth tracking devices?” Streett made a comment.
That has happened in the past. Google and Apple partnered last year to develop Bluetooth coronavirus exposure alerts. In our increasingly interconnected world, managing new dangers will need collaboration.
Technology
Manyroon: The Key to Unlocking Future-Proof Business Solutions

Table of Contents
In the ever-evolving landscape of technology, businesses and industries are constantly seeking innovative solutions to streamline operations, enhance efficiency, and future-proof their processes. One such groundbreaking framework that promises to address these challenges is Manyroon. This transformative system combines interconnectivity, scalability, and adaptability to create a platform that integrates various applications and processes seamlessly across multiple industries. In this article, we will delve into what Manyroon is, how it works, and the impact it has on sectors such as healthcare, manufacturing, education, and entertainment.
What is Manyroon?
Manyroon is a dynamic and scalable framework designed to interconnect systems, processes, and applications across industries. The name “Manyroon” comes from combining “many,” representing the multiplicity of systems and data, and “roon,” which suggests a space or platform with vast possibilities. It aims to bridge gaps between various technologies, facilitating smoother workflows, enhanced communication, and optimized resource management.
At its core, Manyroon focuses on providing businesses with a flexible and cost-effective solution that adapts to their unique needs. By integrating disparate systems, it enhances data accessibility, reduces inefficiencies, and prepares organizations for future advancements in technology.
Core Principles of Manyroon
There are three main principles that define Manyroon: interconnectivity, scalability, and adaptability.
Interconnectivity
The fundamental principle of Manyroon is its ability to link multiple systems and platforms. This interconnectivity ensures that data can flow seamlessly between various applications, devices, and networks. Whether it’s connecting a machine in a factory to a data analytics system or syncing a patient’s health data with a telemedicine platform, Manyroon simplifies the integration of otherwise isolated systems.
Scalability
As organizations grow, their technological needs evolve. Manyroon is built with scalability in mind, meaning that it can accommodate both small-scale operations and large enterprises. The framework can expand as required, ensuring businesses do not outgrow the system. Whether it’s an expanding manufacturing plant or an online educational platform, Manyroon scales to meet the increasing demands of the organization.
Adaptability
Another key feature of Manyroon is its adaptability. As new technologies emerge, Manyroon adjusts without causing disruption to ongoing operations. Whether it’s adopting new AI-driven tools, blockchain solutions, or evolving cybersecurity protocols, Manyroon ensures that businesses can stay ahead of the curve without having to completely overhaul their infrastructure.
Key Features of Manyroon
Manyroon is packed with several key features that contribute to its effectiveness and wide-reaching impact.
- Centralized Data Management: All information from connected systems is stored in a centralized location, making it easier for businesses to access and manage their data. This unified approach reduces the chances of errors caused by fragmented data management.
- Real-Time Synchronization: Manyroon ensures that all connected systems are synchronized in real-time. This eliminates delays in communication and allows for immediate decision-making based on up-to-date information.
- Compatibility Across Industries: Manyroon is versatile and compatible with various sectors, from healthcare to entertainment, manufacturing, and education. It integrates with existing systems and software, ensuring that businesses can leverage the framework without overhauling their entire setup.
- Security Measures: Data security is a top priority. Manyroon includes robust encryption protocols and access controls to ensure that all information exchanged across systems remains protected from cyber threats.
- Cost-Effectiveness: The system is designed to be cost-effective by automating processes, reducing redundancies, and optimizing resource usage. By improving efficiency, Manyroon helps businesses cut operational costs over time.
Applications of Manyroon Across Industries
The versatility of Manyroon allows it to be applied across various sectors. Let’s take a closer look at how it benefits different industries:
Healthcare
In the healthcare industry, Manyroon facilitates the integration of telemedicine platforms, wearable health devices, and electronic health records (EHR). This connected ecosystem allows healthcare providers to monitor patients remotely, gather real-time data, and make informed decisions that improve patient outcomes. Manyroon also plays a crucial role in predictive healthcare, using data analytics to anticipate medical needs and reduce hospital readmissions.
Manufacturing
Manufacturers benefit from Manyroon’s ability to connect machines, sensors, and data analytics platforms. With real-time monitoring and predictive maintenance, Manyroon helps minimize downtime and maximize operational efficiency. In addition, the framework supports inventory management by ensuring that resources are used optimally, reducing waste and unnecessary expenses.
Education
The education sector has seen significant improvements with Manyroon’s integration of digital platforms and personalized learning tools. Teachers can access data on student performance and provide tailored resources that enhance learning outcomes. Furthermore, Manyroon helps facilitate communication between students, educators, and institutions, improving collaboration and resource sharing.
Entertainment
In the entertainment industry, Manyroon optimizes content creation, distribution, and consumption. Whether it’s enhancing the performance of streaming platforms, improving gaming experiences, or supporting virtual reality applications, Manyroon plays a critical role in ensuring seamless digital experiences for users.
How Manyroon Enhances Business Efficiency
Manyroon’s ability to integrate systems and processes leads to enhanced business efficiency in several ways:
- Streamlined Workflow: By eliminating the incompatibilities between different systems, Manyroon helps businesses streamline their workflow, saving valuable time and resources.
- Improved Decision-Making: With real-time data synchronization and easy access to centralized information, businesses can make quicker, more accurate decisions.
- Cost Savings: Manyroon automates tasks and reduces inefficiencies, lowering operational costs while maximizing productivity.
- Seamless Communication: As different departments or business units are connected, communication becomes more efficient, allowing for better coordination and collaboration.
Advantages of Using Manyroon
There are several notable advantages to adopting Manyroon:
- Time Savings: By connecting disparate systems, businesses save time that would otherwise be spent on manual data entry or troubleshooting.
- Flexibility: Manyroon can be tailored to meet the specific needs of any business, whether they’re a small startup or a large corporation.
- Security: With top-notch encryption and data security protocols, Manyroon ensures that sensitive information remains protected at all times.
- Future-Proofing: The adaptability of Manyroon ensures that businesses can continue to evolve with emerging technologies without disruption.
Challenges and Limitations of Manyroon
Despite its numerous advantages, there are some challenges businesses may face when adopting Manyroon:
- Initial Setup Costs: Implementing Manyroon may require significant upfront investment in terms of both time and money.
- Security Risks: If not properly managed, interconnected systems may present security vulnerabilities.
- Learning Curve: Users who are not familiar with integrated systems may face a learning curve during the initial adoption phase.
The Future of Manyroon
The future of Manyroon looks promising, with continued developments in AI, machine learning, and blockchain likely to enhance its capabilities. As industries continue to digitalize, Manyroon will play a crucial role in supporting smart cities, sustainable development, and other futuristic applications.
Conclusion
In conclusion, Manyroon is a revolutionary framework that is reshaping how industries operate by integrating diverse systems, ensuring scalability, and adapting to future technological advancements. Whether in healthcare, manufacturing, education, or entertainment, Manyroon offers businesses the tools they need to improve efficiency, reduce costs, and stay competitive in an ever-changing landscape. As industries continue to embrace digital transformation, Manyroon is poised to be a key player in driving that change.
FAQs
What is Manyroon?
Manyroon is a scalable framework that connects diverse systems and processes, enabling seamless integration across industries to improve efficiency and adaptability.
How does Manyroon improve business efficiency?
It streamlines workflows, enhances real-time data access, and reduces redundancies, leading to faster decision-making and cost savings.
Can Manyroon be used across all industries?
Yes, Manyroon is versatile and applicable in sectors like healthcare, manufacturing, education, and entertainment, offering tailored solutions for each.
Is Manyroon secure for handling sensitive data?
Yes, Manyroon incorporates strong encryption protocols and access controls, ensuring the secure exchange of data across connected systems.
What are the main benefits of adopting Manyroon?
Adopting Manyroon leads to time savings, improved decision-making, cost reduction, and future-proofing against emerging technologies.
Social Media
Igagony: The Ultimate Tool for Private Instagram Story Viewing

Table of Contents
In today’s digital world, social media platforms like Instagram are an essential part of our daily lives. However, sometimes you might want to view stories without logging in or revealing your identity. This is where Igagony comes in—an online tool designed to allow users to view and download Instagram stories anonymously. In this article, we’ll dive into what Igagony is, its features, how to use it, and its privacy advantages.
What is Igagony?
Igagony is an online service that enables users to anonymously view Instagram stories without needing to create or log into an Instagram account. With its simple interface and ease of use, Igagony allows you to explore the latest stories from public Instagram profiles without any hassle or risk of revealing your identity.
Key Features of Igagony
- Anonymous Viewing: One of the biggest advantages of Igagony is its ability to allow users to view Instagram stories without disclosing any personal information. The tool ensures complete anonymity, meaning you can enjoy stories without being tracked or identified.
- No Instagram Account Required: Unlike traditional Instagram usage, where you need an account to view stories, Igagony removes that requirement. This is perfect for users who do not want to create an Instagram profile or who prefer not to use their own account to view others’ stories.
- Compatibility: Igagony works on various devices and platforms, including Windows, macOS, iOS, and Android. Whether you are on a desktop or using your smartphone, you can access and use Igagony seamlessly.
- Story Downloading: If you want to keep an Instagram story for offline viewing, Igagony allows you to download it directly from the tool. This feature makes it a great choice for those who want to save content for future reference.
Privacy and Security
One of the standout features of Igagony is its focus on privacy and security. Here’s what makes it a safe and secure option:
- No Data Tracking: Igagony does not track your activities or store any browsing history. Once you finish using the service, no trace of your visit remains, ensuring that your actions are not monitored or logged.
- No Personal Information Needed: The platform does not ask for any personal details. This guarantees that you can use the service entirely anonymously, protecting your privacy.
Limitations of Igagony
While Igagony offers many benefits, there are some limitations to be aware of:
- Public Profiles Only: Igagony can only retrieve stories from public Instagram profiles. If a user has a private account, their stories will not be accessible through this tool.
- Story Viewing Only: Igagony is designed specifically for viewing and downloading Instagram stories. If you’re looking to access other content like Instagram posts or reels, this tool will not be suitable.
Advantages of Using Igagony
- Convenience: Igagony is incredibly user-friendly. You can access the platform quickly and enter the Instagram username to view and download stories within moments.
- No Installation Required: Unlike some other tools, Igagony doesn’t require any downloads or installations. This makes it a hassle-free option for users who want quick access without setting up new software.
- Free to Use: Igagony is completely free, meaning you don’t have to worry about any subscriptions or hidden fees. Whether you want to view one story or many, you can do so without spending a dime.
How to Use Igagony
Using Igagony is straightforward and doesn’t require any technical knowledge. Here’s how you can get started:
- Open the Igagony Website: Navigate to the Igagony website from your browser.
- Enter the Instagram Username: Type in the username of the Instagram account whose stories you want to view.
- Browse and Select the Story: Once the profile is loaded, you can browse through the available stories. Simply click on the one you wish to watch.
- Download (Optional): If you want to save a story, Igagony provides an option to download it to your device for offline viewing.
Igagony is compatible with multiple devices, making it easy to use on both desktops and mobile devices.
Privacy Considerations
Igagony is built with privacy in mind, but it’s still essential to be aware of how you use the platform. Since the service does not require any personal information, you remain anonymous when using it. However, users should respect Instagram’s terms of service, especially regarding the downloading and sharing of content. Make sure to use the tool responsibly and avoid violating the platform’s rules.
Alternatives to Igagony
There are other services similar to Igagony that allow anonymous viewing and downloading of Instagram stories. Some alternatives include:
- InstaStory
- StoriesIG
- StorySaver
Each of these tools has its own set of features, but Igagony is often preferred for its simplicity and the fact that it doesn’t require users to log into Instagram.
Conclusion
Igagony is a valuable tool for anyone looking to view and download Instagram stories anonymously. It offers a convenient, easy-to-use, and free service, with an emphasis on privacy and security. While it is limited to public profiles and story content only, it remains a reliable choice for those who want a hassle-free experience. Whether you’re exploring Instagram for entertainment or saving stories for later, Igagony provides a straightforward way to do so without compromising your privacy.
FAQs
Is Igagony free to use?
Yes, Igagony is completely free, and there are no hidden fees or subscriptions required to view or download stories.
Can I view stories from private Instagram accounts?
No, Igagony can only access stories from public Instagram profiles, and private accounts are not supported.
Do I need an Instagram account to use Igagony?
No, you do not need an Instagram account to use Igagony, as it allows anonymous viewing of stories.
Can I download Instagram stories using Igagony?
Yes, Igagony allows you to download Instagram stories for offline viewing directly from the platform.
Is my personal information safe while using Igagony?
Igagony does not require personal information, ensuring that your privacy is maintained during use.
Technology
Tech-UB.57.001: The Game-Changing Innovation in Technology and Education
Table of Contents
Tech-UB.57.001 is an innovative concept that applies both to a cutting-edge technology platform and an academic course at New York University (NYU). While the technology aspect focuses on improving business efficiency, security, and scalability, the university course aims to bridge the gap between business and technology, preparing students for the evolving tech landscape.
This article will explore both aspects of Tech UB.57.001, detailing its features, applications, benefits, and impact.
Tech-UB.57.001 as a Technology
Tech-UB.57.001 is an advanced technology designed to improve business operations, increase efficiency, and ensure security. Many industries have adopted it to handle high-speed data processing, automate tasks, and manage workflows.
Key Features of Tech-UB.57.001 Technology
- High-Speed Processing – This technology ensures fast execution of tasks, reducing waiting times and improving overall efficiency.
- Scalability – It is adaptable to businesses of all sizes, from startups to multinational corporations.
- User-Friendly Interface – The system is designed to be simple and intuitive, making it easy for users to integrate it into existing operations.
- Enhanced Security – Advanced encryption and security protocols protect sensitive data from cyber threats.
- Cost-Effectiveness – Businesses benefit from its high value without overspending on expensive IT infrastructure.
Industries Benefiting from Tech-UB.57.001
- Healthcare – The technology helps manage patient records securely, streamlines hospital operations, and enhances diagnostics.
- Manufacturing – Companies use it to track inventory, optimize production, and improve supply chain management.
- Retail – Businesses analyze consumer behavior, manage stock more efficiently, and improve customer service through data-driven decisions.
- Artificial Intelligence (AI) – Tech-UB.57.001 powers AI-driven tools, helping businesses automate repetitive tasks and make intelligent predictions.
Impact on Businesses
By adopting this technology, businesses experience:
- Better operational efficiency, leading to reduced costs and increased profits.
- Real-time analytics, helping companies make informed decisions.
- Improved security, ensuring compliance with regulations and protecting sensitive information.
Tech-UB.57.001 as an Academic Course at NYU
Aside from being a powerful technology, Tech UB.57.001 is also a well-structured academic course at New York University (NYU). The course focuses on technology and business integration, preparing students for modern challenges in the tech industry.
Course Overview
Tech-UB.57.001 at NYU is designed to help students develop both technical and business skills. It is a highly practical program, incorporating real-world applications, case studies, and industry collaborations.
What Students Learn
- Technology Fundamentals – Covers programming, systems design, and data analysis.
- Business Applications – Explores how companies use technology for productivity and innovation.
- Project-Based Learning – Students work on real-world projects to apply their knowledge in business settings.
- Industry Networking – Provides opportunities to connect with professionals, attend guest lectures, and secure internships.
Who Should Enroll?
- Business Professionals – Individuals seeking to integrate technology into their business models.
- Tech Enthusiasts – Those interested in understanding how technology drives business success.
- Aspiring Entrepreneurs – People looking to launch tech startups or develop innovative solutions.
Assessment Methods
- Exams – Test theoretical knowledge of technology and business principles.
- Projects – Allow students to solve practical challenges using technology.
- Group Work – Encourages collaboration and teamwork, which are essential for modern businesses.
Key Benefits of the Course
- Career Readiness – Graduates gain skills that prepare them for various roles in the tech industry.
- Industry Relevance – The curriculum is updated regularly to match current industry demands.
- Diverse Career Paths – Students can pursue careers in project management, data analytics, software development, and tech consulting.
Why Tech-UB.57.001 Matters
Whether as an advanced technology or an educational course, Tech-UB.57.001 is making a significant impact.
For Businesses
- It enhances operations, improves security, and drives innovation.
- Companies using Tech-UB.57.001 gain a competitive edge by optimizing workflows and increasing efficiency.
For Students
- The course equips students with practical skills, making them more attractive to employers.
- It helps future entrepreneurs understand how technology shapes business success.
Conclusion
Tech-UB.57.001 is an influential concept that blends technology and education. As a technology, it enhances business efficiency, security, and automation. As an academic course, it prepares students for the tech-driven job market by providing hands-on experience, real-world applications, and career opportunities.
Whether you are a business owner looking for tech solutions or a student aiming to gain valuable skills, Tech-UB.57.001 offers a path to success in the modern digital world.
FAQs
What is Tech-UB.57.001 used for?
It is both a technology improving business operations and a course at NYU integrating tech and business education.
How does Tech-UB.57.001 benefit businesses?
It enhances efficiency, security, and automation, making operations faster, smarter, and cost-effective.
Who should take the Tech-UB.57.001 course at NYU?
Business professionals, tech enthusiasts, and aspiring entrepreneurs looking to integrate technology into their careers.
What industries benefit the most from Tech-UB.57.001 technology?
Healthcare, manufacturing, retail, and AI-driven sectors that require automation and data security.
What skills do students gain from the Tech-UB.57.001 course?
Tech fundamentals, business strategy, problem-solving, and hands-on project experience for career growth.
-

 Travel4 years ago
Travel4 years agoThe Family of Kirk Passmore Issues a Statement Regarding the Missing Surfer
-

 Technology3 months ago
Technology3 months agoManyroon: The Key to Unlocking Future-Proof Business Solutions
-

 Cryptocurrency1 year ago
Cryptocurrency1 year agoBest Tips For Cryptopronetwork com Contact 2024
-

 Technology3 years ago
Technology3 years agoPaturnpiketollbyplate Login & Account Complete Guide Paturnpike.com
-

 Apps & Software2 years ago
Apps & Software2 years agoFapello 2023: Social Media Platform for NSFW Content
-

 Business3 months ago
Business3 months agoCoyyn.com Gig Economy: Smart Contracts and Fair Payments for Freelancers
-

 Business4 months ago
Business4 months agoAcumen: The Key to Smart Decision-Making and Success
-
 Technology4 months ago
Technology4 months agoEaton Z-SCH230/40-40 Brummt? Causes, Fixes, and Solutions






